Security Services

Security Service Portfolio:
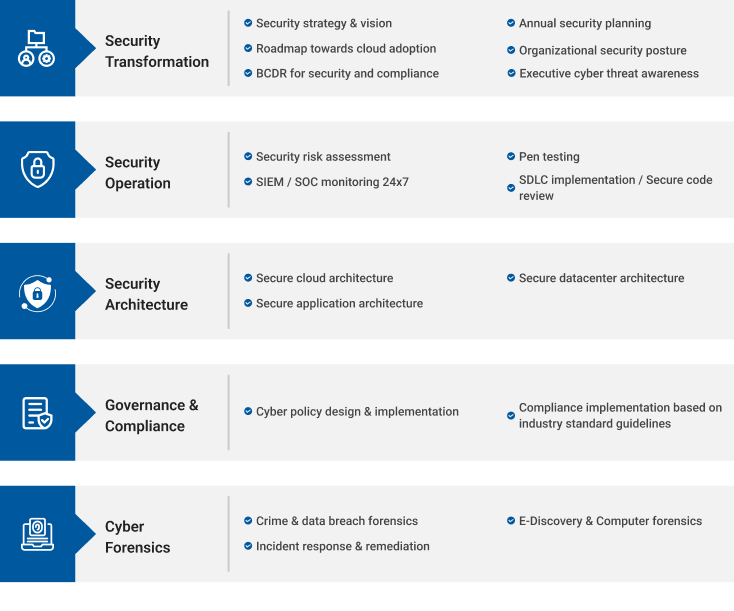
Security, Identity Management, Authentication:
Security, Identity Management, Authentication: We provide consulting services in identity management and authentication.
- Conduct security validation and review the reference architectures.
- Audit and certify the compliance of various systems (Windows, Linux, Network Devices and peripherals)
- Validate security configurations and access to security infrastructure tools, including, firewalls, IDS/IPS, WAFs and anti-malware/endpoint protection systems.
- Conduct and facilitate threat modelling of services and applications that tie to the risk and data associated with the service or application.
- Ensure a complete, accurate and valid inventory of all systems, infrastructure and applications that should be logged by the Security Information and Event Management (SIEM) or log management tool.
- Design cloud and security solutions, to facilitate the effective transition and migration of projects and programs into unique and adaptive cloud environment (AWS/ MS Azure/ GCP).
- Vulnerability Management and Cloud Security using SOAR and SEIM
Application Security:
We partner with Virsec (https://www.virsec.com) which delivers a new approach to security and their platform is solving solve complex security challenges for governments, defense, technology, industry control systems, financial services, healthcare, etc. Key features of Virsec:
- Vulnerability mitigation & exposure management - Core value proposition of "patchless mitigation". The AI-enabled platform – ottoguard.ai helps significantly reduce the number of vulnerabilities customers need to address through traditional patching methods, aiming for a tangible ROI and faster time-to-value.
- Ransomware protection
- Legacy software protection
- Makes applications self-defending during runtime
how can we help you?
Contact us at the Consulting WP office nearest to you or submit a business inquiry online.
